Cloud Account¶
Onboarding your Cloud Accounts¶
To configure your own account, you can grant us a security role through different mechanisms to provision infrastructure on your behalf. If you wish to host on our account, you can skip this step.
Here is how it looks like:
- For AWS, we have a 1-click integration to create your Cloudformation stack. For step-by-step instructions, here is a link to the video
- For GCP, we have a 1-click integration using Cloud Shell to create the security role. For step-by-step instructions, here is a link to the video
- For Azure, we have a 1-click integration using Azure Cloud Shell to create the security role. For step-by-step instructions, here is a link to the video
Note
If you encounter any error due to the already created AWSLoadBalancerControllerIAMPolicy policy in AWS, please select the option to onboard your AWS account without creating that policy
Required permissions for onboarding¶
Permissions required to execute account onboarding vary depending on the cloud provider.
AWS¶
User executing the CloudFormation stack needs to have AdministratorAccess on the AWS account.
GCP¶
User executing the Cloud Shell script needs to have roles/owner on the GCP project.
Azure¶
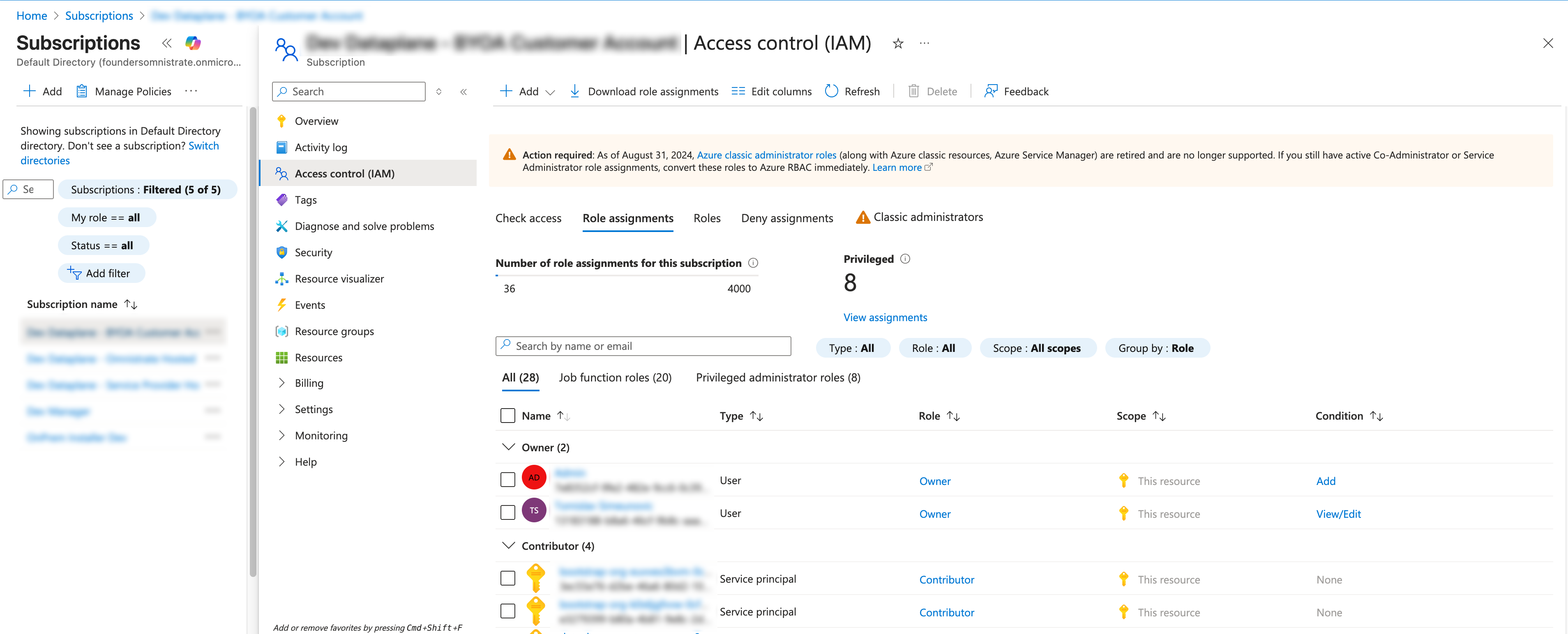
User executing the Cloud Shell script needs to either be an Owner on the Azure subscription, or have the following roles: - User Access Administrator - Application Administrator
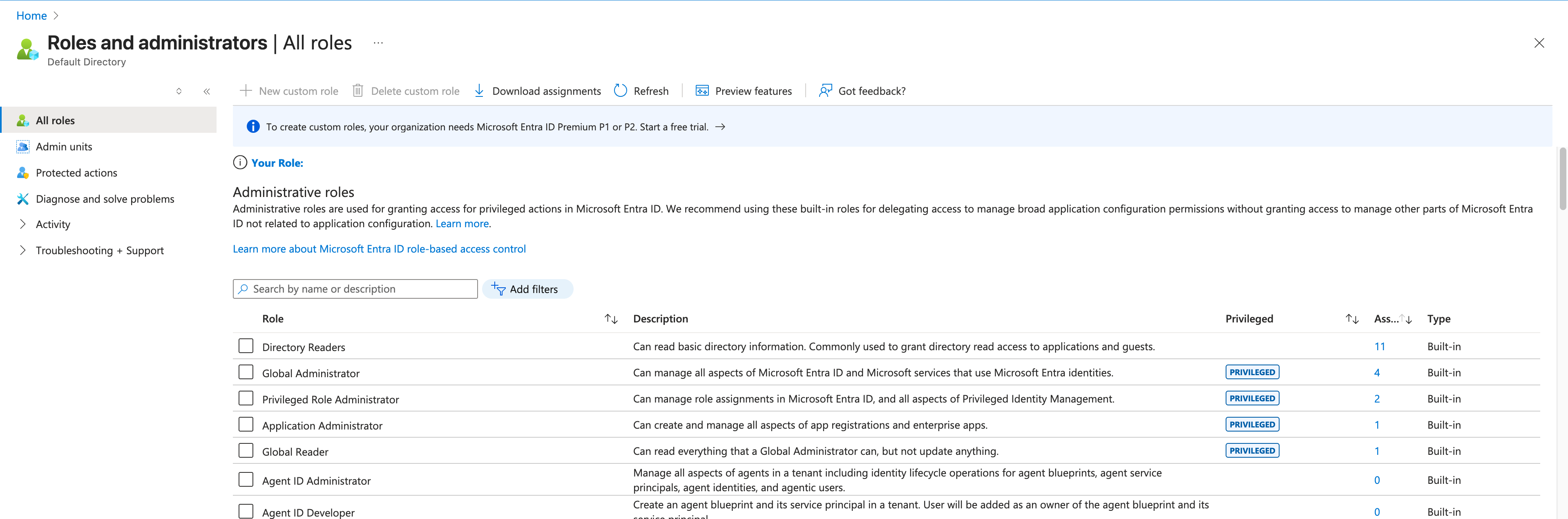
In addition, there are permissions required on the Azure AD level: - Privileged Role Administrator
Common Issues During Account Onboarding¶
AWS Load Balancer Controller Policy Already Exists¶
Problem: AWS accounts sometimes have the AWS Load Balancer Controller Policy already installed, which can result in CloudFormation stack errors due to duplicate policy creation attempts.
Solution: When onboarding your AWS account, if you encounter errors related to the AWS Load Balancer Controller Policy already existing, you need to configure the CloudFormation parameter to skip the policy installation.
During the AWS account onboarding process:
- Set the CloudFormation parameter for AWS Load Balancer Controller Policy creation to
false - This will skip the installation of the policy and avoid the duplicate resource error
- The existing policy in your account will be used instead
Cloud Account already used in different Environment¶
Problem: You used a cloud account to one Omnistrate Organization and later attempted to add it to a different Omnistrate Organization, which resulted an error message.
Solution: This is expected behavior. The same cloud account can be used across different environments (dev, staging, prod) within the same organization, but cannot be used across different organizations. This is a security feature to prevent account conflicts and ensure proper isolation between organizations.
If you need to use the same cloud account across different organizations, you'll need to:
- Remove the account from the first organization
- Wait for the removal to complete
- Add it to the second organization
Offboarding¶
To offboard a Cloud Account, please follow the steps in order:
- Delete the account config here to clean up all the Omnistrate created artifacts
- Wait for account config to be deleted on the Omnistrate Portal
- For AWS you can delete the CloudFormation used to onboard
- For GCP you can call the offboarding script using CloudShell
- For Azure you can call the offboarding script using CloudShell
For any questions, please reach out to us at support@omnistrate.com